Dynamic DNS update script for IPv6
IPv6 works a bit differently than IPv4.
Previously, each Router got only one IPv4 address, then created a private network, waiting for clients to connect via it's ports, or later the WiFi. When a new device connected, it got a local address like 192.168.1.101 - and a gateway and DNS address, usually the router's local address, e.g. 192.168.1.1. When the computer wanted to go out to the internet, it had to connect to the modem first, which masked the inside addresses, and "acted" if it was sending the messages, translating between the local and the global network.
This had a few side effects. If you wanted to open a port to the outside world, you either had to set it up through the router's configuration interface, or you could use UPnP commands. Also your devices inside the networks were more protected, as the router acted as a firewall between the world and your computer.
IPv6 is different as addresses are not scarse so when a modem registers itself it actually gets an address range instead of a single address.
If a new device connects to your modem/router it registers itself in the global network via the modem's DHCP, so it can be reached directly from the internet. This also means, that from now on your device is exposed to the internet directly, so it may be more vulnerable to attacks from the open. In some cases the modem/router may still have firewall rules enabled though so keep an eye out!
In some systems you have to manually enable support for IPv6. For digital ocean's droplets: check this article out
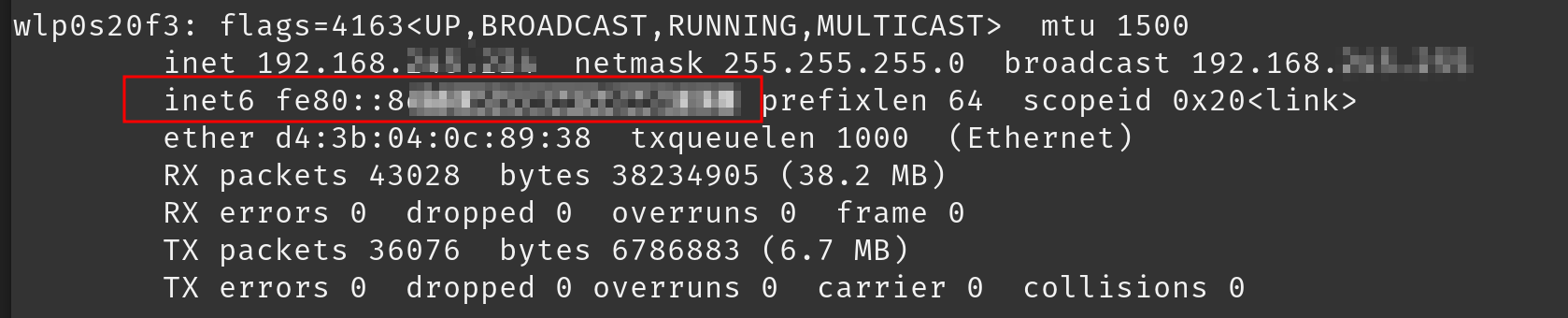
- Once you checked your router's settings, run
ifconfigto check your IPv6 address.
- Reg an account on dynv6.net
- Create a script as
/home/pi/dnsupdate.shwith the content below - Change permissions, so it's runnable:
chmod +x /home/pi/dnsupdate.sh - Run
crontab -eand add the following line for running the script every 5 minutes:*/5 * * * * /home/pi/dnsupdate.sh
You may want to look into how to make your [raspberry pi secure](./Rasbperry PI security)!
/home/pi/dnsupdate.sh
#!/bin/sh -e
hostname="ADDRESS.dynv6.net"
token="TOKEN_FROM_dnyv6.net"
file=$HOME/.dynv6.addr6
[ -e $file ] && old=`cat $file`
if [ -z "$hostname" -o -z "$token" ]; then
echo "Usage: token=<your-authentication-token> [netmask=64] $0 your-name.dynv6.net [device]"
exit 1
fi
if [ -z "$netmask" ]; then
netmask=128
fi
if [ -n "$device" ]; then
device="dev $device"
fi
address=$(ip -6 addr list scope global $device | grep -v " fd" | sed -n 's/.*inet6 \([0-9a-f:]\+\).*/\1/p' | head -n 1)
if [ -e /usr/bin/curl ]; then
bin="curl -fsS"
elif [ -e /usr/bin/wget ]; then
bin="wget -O-"
else
echo "neither curl nor wget found"
exit 1
fi
if [ -z "$address" ]; then
echo "no IPv6 address found"
exit 1
fi
# address with netmask
current=$address/$netmask
if [ "$old" = "$current" ]; then
echo "IPv6 address unchanged"
exit
fi
# send addresses to dynv6
$bin "http://dynv6.com/api/update?hostname=$hostname&ipv6=$current&token=$token"
$bin "http://ipv4.dynv6.com/api/update?hostname=$hostname&ipv4=auto&token=$token"
# save current address
echo $current > $file
My old IPV4 update script
I use this funny dns server dyndns.hu instead of hooking up my own, because that's an extra few hours I assume...
RESPONSE=$(curl -d "username=$USER&domain=dyndns.hu&password=$PASS" https://www.dyndns.hu/login.php)
if [ $RESPONSE == *"Sikeres"* ](wikilink://%20%24RESPONSE%20%3D%3D%20*%22Sikeres%22*%20); then
echo "Success IPV4!"
else
echo "Error."
fi